As Seen On

Secure Access Service Edge: Your Complete SASE Readiness Checklist for Regulated Industries
Download Blueclone's Secure Access Service Edge Checklist
The Growing Need for SASE Cybersecurity as Data Moves Beyond the Traditional Office Perimeter
Navigating the ever-tightening regulatory environment poses a challenge for organizations in healthcare, finance, law, and related fields. Today, data does not simply reside within office walls, it flows between remote employees, clients, cloud platforms, and mobile devices, creating endless possibilities for innovation but also countless opportunities for risk. If you oversee security or compliance for a small to mid-sized business in New Jersey or the greater Northeast, understanding secure access service edge (SASE) is no longer optional. It’s mission-critical.
In this guide, you’ll discover what secure access service edge (SASE) means for SMBs, including the essential components of a successful implementation and a comprehensive checklist to assess your organization’s readiness. You’ll learn why more companies are relying on managed SASE solutions to safeguard their network edges and ensure compliance. Plus, if your organization is transitioning to hybrid work, adopting cloud applications, or preparing for an audit, you’ll find actionable insights to future-proof your cybersecurity and maintain seamless, real-time access for your team.

Understanding Secure Access Service Edge: SASE Meaning, Fundamentals, and Emergence in Regulated SMBs
The acute risks faced by regulated industries like healthcare, legal, and insurance firms demand a different approach to cybersecurity and network management. Traditional perimeters can no longer safeguard information in an environment where users, devices, and applications are everywhere. That’s where secure access service edge steps in as a transformative concept.
SASE meaning centers on converging two previously separate IT domains: network connectivity and information security. Instead of firewalls and VPNs tied to office hardware, SASE delivers a unified, identity-driven, cloud-native platform. Every American Bar Association rule, HIPAA safeguard, or SEC policy that applies in your industry follows users and devices wherever they operate.
In practical terms, SASE cybersecurity does not just bolt on new tools. It re-architects your digital landscape so that security policies are enforced in real time, in line with every access attempt, file transfer, or cloud application login, regardless of whether work happens at a central NJ office, a home WiFi connection, or on a client site. Identity and context drive every access decision.
Why is this shift essential for SMBs? The complexity of compliance frameworks like PCI-DSS, FINRA, HIPAA, and SOX has soared as cyber criminals exploit the chaos of cloud sprawl and hybrid work. Simple VPNs and office-bound firewalls cannot keep pace. Instead, regulated organizations now require a flexible, zero-trust security architecture that works everywhere, at every moment, on every device.
Organizations throughout Central New Jersey and beyond are recognizing that SASE is not a buzzword. It’s a strategic upgrade that enables both compliance and growth by centralizing policy management, improving real-time risk visibility, tightening access controls, and reducing technological fragmentation.
Non-Negotiable SASE Benefits for Compliance, Performance, and Growth
If you’re leading IT or compliance for a medical group in Trenton, a boutique finance firm in Princeton, or a regional law office in Mercer County, NJ, you’ve already felt the strain of meeting both client expectations and government mandates. The commitment to compliance is never just about passing the next audit. Instead, it’s about maintaining client trust, reputation, and uninterrupted business operations through each threat or regulatory change.
SASE benefits revolutionize this balancing act by:
- Enabling Zero Trust at Scale: Every identity, device, and app session is authenticated and authorized, making policies adaptive and context-driven rather than reliant on fixed networks or outdated assumptions.
- Delivering Cloud-Native Agility: Bring new teams, remote offices, third-party partners, and SaaS solutions online quickly, governed under a uniform security framework. No more security holes from “shadow IT.”
- Reducing Attack Surface: Legacy overlap and tool sprawl (firewalls, endpoint protection, VPNs) leave gaps. SASE consolidates technology, minimizes redundancy, and shrinks opportunities for attackers.
- Streamlining Auditable Compliance: Real-time monitoring, centralized logs, and detailed reporting make preparing for audits under HIPAA, FINRA, SOX, PCI, or others far less grueling.
- Supporting Strategic Scalability: As your business grows, SASE allows IT to spin up new offices or remote work scenarios without risky shortcuts or heavy manual configuration.
- Enhancing User Experience: Employees, contractors, and clients gain fast, secure access from anywhere, with no more sluggish VPNs or endless password resets.
A recent Gartner analysis reported that companies deploying SASE architectures reported lower breach frequencies, improved audit outcomes, and higher agility during digital transformations. For regulated SMBs, this shift levels the playing field with enterprise security capabilities, at a cost and complexity suited for smaller organizations.

The SASE Readiness Checklist: Action Steps for Regulated SMBs
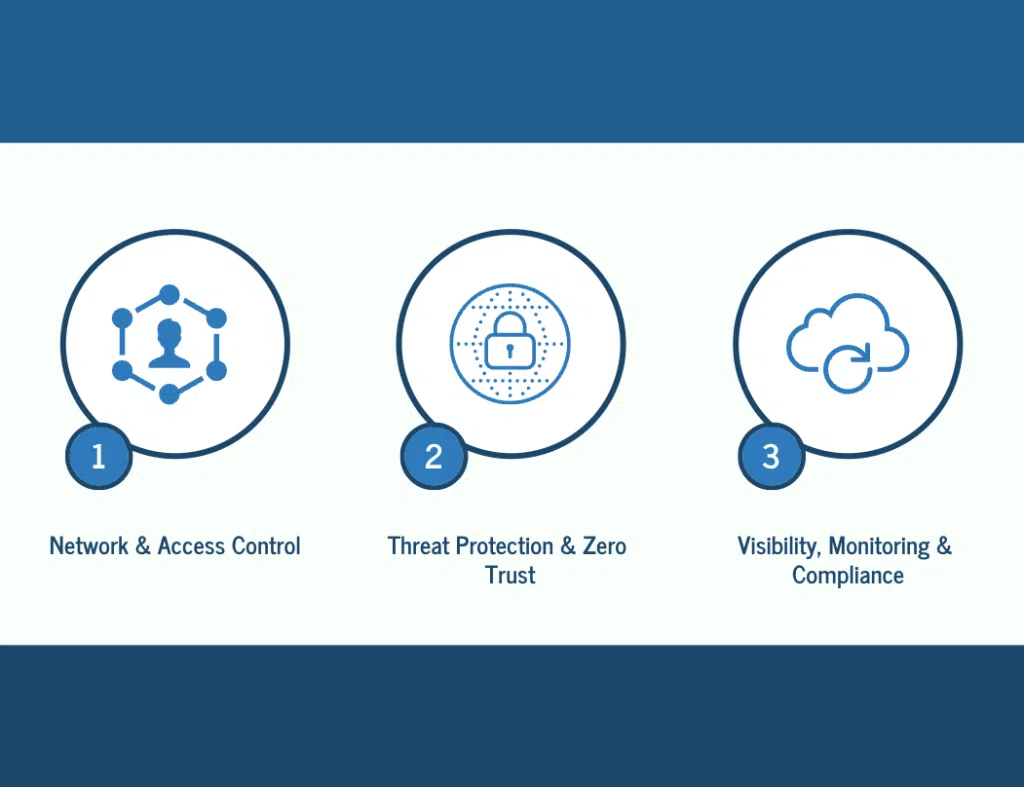
Transitioning to SASE security isn’t just about buying a new firewall replacement. It requires a methodical review, strong leadership buy-in, and partnership with SASE providers who understand how to simplify security for regulated businesses. The following checklist, drawn from real deployments across Central New Jersey, helps both technical and business leaders map what’s needed for safe, cost-effective migration.
1. Network & Access Control
Map Every Connection: Prepare an inventory of all users, devices, cloud services, VPN links, and potential “shadow IT.” Missed endpoints, like remote laptops or unsanctioned SaaS accounts, constitute your greatest risk exposure.
Eliminate Redundancies: Audit your gateways and firewalls. Decommission obsolete devices and centralize configuration control, minimizing overlooked vulnerabilities.
Mandate Identity-Driven Access: Move from generic shared accounts or static passwords to unique, multi-factor authentication for all staff, partners, and vendors. This ensures only verified identities access protected resources, wherever they work.
2. Threat Protection & Zero Trust
Unify Security Functions: Replace disparate vendor tools (separate firewall, web filter, cloud broker) with a single platform that applies rules consistently and can enforce least-privilege access by default.
Implement Live, Real-Time Traffic Inspection: Interrupt threats and policy violations as they happen, not hours or days after the breach. SASE solutions scan both cloud and internal network traffic continuously, alerting IT staff in seconds if policy is violated.
Deploy Adaptive Policies: Security rules should change depending on device health, geographic anomalies, and context, blocking high-risk connections automatically.
3. Visibility, Monitoring & Compliance
Ensure Compliance Alignment: Does your chosen solution support compliance with HIPAA, PCI-DSS, or SOC 2? Ask about out-of-the-box policy templates and documentation designed for regulatory review.
Centralize Audit Logging: All policy changes, incident alerts, and access grants should be logged and easily exportable for auditor review.
Monitor Globally: Use dashboards that reveal user and session behavior, file movement, and SaaS usage across hybrid and remote setups.
From Checklist to Real-World SASE Security: Solutions for Healthcare, Financial, and Legal SMBs

Ready to bridge theory with practice? Let’s look at practical examples of SASE deployment in different regulated sectors:
Healthcare Organizations:
A regional medical group with five locations in Central New Jersey must comply with HIPAA and ensure patient records are accessible for telehealth. However, they’ve suffered growing pains as remote work and EHR cloud adoption outpace legacy VPNs and fragmented endpoint tools. By moving to a SASE platform:
- Medical records and communication apps are protected with end-to-end encryption and context-aware policies that don’t sacrifice user convenience.
- New clinics and providers are onboarded securely in days, not weeks.
- Annual HIPAA audits are passed with detailed SIEM logs, reducing compliance workload for IT.
Financial Firms:
Registered investment advisers in Princeton face ongoing challenges around SEC/FINRA demands and complex workflows across remote brokers and cloud trading portals. SASE:
- Centralizes policy management, so every credential or device change instantly propagates everywhere.
- Enables encrypted, policy-driven access to analytics, transaction records, and client files, without trusting local devices or risking unauthorized data extraction.
- Provides detailed audit trails, expediting regulatory review without disrupting daily operations.
Law and Legal Practices:
Smaller legal partnerships and regional firms struggle to maintain client confidentiality as they embrace hybrid work and collaborative discovery processes. By leveraging SASE cybersecurity:
- File transfers, matter discussions, and research data remain protected, even when accessed from home offices or courtrooms.
- External experts or collaborators receive time-limited, policy-governed access, and audit logs track every document opened or shared for court or compliance review.
No matter the vertical, SASE security transforms compliance from a last-minute scramble to a routine, automated process, while reducing the friction that often frustrates technology users.
How to Choose the Right SASE Provider:
A Buyer’s Primer for Regulated SMBs
With SASE becoming central to compliance and operational strategy, selecting a trusted provider is pivotal. Not all SASE vendors are equipped to handle the unique challenges or regulatory nuances of SMBs in healthcare, law, or finance.
What should you look for in potential SASE providers?
- Deep Regulatory Expertise: Before selecting a platform, ask whether the provider supports compliance frameworks relevant to your field (HIPAA for healthcare, SOX for finance, etc.). Ask for proof of successful audits or case studies.
- Technology Stack: Opt for a provider offering a complete SASE stack, combining SD-WAN, Zero Trust, cloud web gateways, firewalls, DLP, and security broker functionality in a unified portal.
- Local and Responsive Support: When an incident occurs, a rapid, informed response is critical. Providers with regional support (as found at Blueclone Networks) can deliver hands-on deployment and compliance consulting.
- Transparent SLAs and Reporting: Clear service level agreements (uptime, notification times, breach response) should be standard, not optional.
- Customizable Integration and Scalability: The right solution should plug into your existing directories (Active Directory, Azure AD), SaaS portfolios, and be ready for new locations or growing staff.
- Audit-Ready Logging and Reporting: Automated logging, policy version histories, and one-click audit exports simplify regulatory reviews and client reporting.
For firms with limited in-house IT, managed SASE offerings streamline the complexity: They offload daily administration, routine monitoring, and compliance updating, so internal staff focus on value-driving activities.
In New Jersey and the Northeast, a partnership with a provider like Blueclone Networks can mean the difference between reacting to incidents and proactively managing risk. Book an initial Discovery meeting to see how a local SASE expert can align security with your operational goals.

SASE Deployment: Best Practices from Migration to Maintenance
A successful SASE transition doesn’t have to be disruptive. Whether rolling out to the entire firm or piloting with a remote office, following these SASE migration best practices eliminates common pitfalls and maximizes ROI:
1. Baseline Assessment & Stakeholder Engagement
Start by mapping systems, workflows, third-party integrations, and compliance assets (e.g., medical devices, cloud archives, client portals). Involve department managers and compliance leaders early, ensuring buy-in and alignment.
2. Gap Analysis
Review the effectiveness of legacy defenses. Where are VPNs struggling to serve remote users? Where does a lack of endpoint visibility put confidential records at risk? Map these shortcomings to regulatory and business needs.
3. Solution Design
Define technical requirements for identity management, device security, SaaS integrations, and compliance reporting. Shortlist SASE solutions that demonstrate success with organizations of your size and within your industry.
4. Pilot and Validate
Deploy the solution with a non-critical department or location. Monitor user experience, performance, and compliance reporting. Adjust policies and controls as required.
5. Full Deployment & Continuous Improvement
Roll out SASE organization-wide in phases. Schedule regular optimization reviews, track compliance posture, and update awareness training for leaders and end-users.
Common Pitfalls to Avoid:
- Launching SASE without sufficient training or change management can lead to poor user adoption and unintentional risk.
- Failing to integrate with existing IT management or compliance workflows may cause reporting or audit challenges.
- Ignoring the impact of new workflows on end-user experience can create frustration, ensuring interfaces are intuitive and support is readily available is key.
SASE Security vs. Traditional Network Security: A Comparative Look
In the past, small and mid-sized businesses built their defenses with on-premises firewalls, VPN concentrators, and locally managed anti-virus tools. In 2026, these solutions are showing their age.
Key advantages when comparing SASE vs. legacy architectures:
- Universal Coverage: SASE applies consistent security and compliance controls over every user and device, no matter their location or network.
- Reduced Management and Risk: Instead of juggling vendors and patching individual tools, one managed platform reduces complexity, patchwork failures, and hidden gaps.
- Lower Cost of Ownership: Less hardware, less manual upkeep, and a scalable cloud subscription model mean predictable budgeting and easier expansion for new locations, contractors, or cloud apps.
- Always Audit-Ready: Centralized visibility and live reporting prepare you for surprise audits at any time, lowering the stress and cost of regulatory review.
- Built for Hybrid and Cloud Work: As you expand cloud services or support remote/hybrid teams, the right SASE framework scales with you, without new infrastructure or licenses every time you grow.
More organizations now choose to work with SASE providers that integrate with hybrid and multi-cloud environments (e.g., AWS, Microsoft Azure, Google Cloud). This ensures uniform compliance and security, even when regulatory documentation or client contracts require rapid adaptation.
A recent 2026 assessment in CSO Online highlighted firms gaining 30–50% management time savings after consolidating to a single SASE stack, for law offices, pharmacies, and boutique finance offices alike.
SASE Trends and the Impact of AI-Driven Automation
Looking ahead, SASE security frameworks are evolving rapidly, especially for organizations in compliance-heavy industries. Modern SASE stacks increasingly offer:
- Zero Trust at Every Layer: Risk-based, adaptive policies become standard, reducing over-broad access and improving response to anomalies.
- Automated Incident Response: AI modules detect and neutralize threats faster than manual intervention, closing gaps before attackers can exploit them.
- Predictive Compliance: Machine learning tracks where policies are drifting, so SMBs stay ahead of auditors and avoid lapses between assessments.
- Seamless, Location-Independent User Experience: SASE makes “work from anywhere” not only secure but also easy for users, no more sluggish connections or access headaches.
This next-generation approach lets organizations become both more effective in compliance and more ambitious in digital transformation plans, without taking on unsustainable risk or technical debt.
Unlock Your Secure Access Service Edge Advantage
Adopting SASE is a strategic transformation, not a tactical stopgap. As hybrid work, regulatory requirements, and cloud adoption continue their relentless march, SMBs that embrace SASE are better positioned to secure data, serve clients, and support continuous growth.
Checklist for getting started:
- Download your SASE Readiness Checklist: The tool is customized for regulated industries and gives a step-by-step plan for compliance and security assessment.
- Book an initial Discovery meeting with Blueclone Networks: Get a handshake, not a hard sell. Discuss your business model, get actionable advice, and receive a compliance roadmap tailored to your business objectives.
- Plan your first SASE pilot: Whether it’s one department, a remote office, or moving sensitive data to a SaaS platform, test and measure results before scaling up.
- Audit and optimize: Use your checklist and provider consultations to maintain security parity as you grow, add cloud apps, or prepare for new compliance challenges.
- Stay informed and adaptive: SASE trends, cyber risk profiles, and regulatory expectations evolve. Join regional IT forums, subscribe to SASE news, and build a relationship with hands-on, responsive experts.
SASE Security in Action: Common Use Cases for Regulated SMBs

Understanding Secure Access Service Edge is easier when you see it in real-world scenarios. Here are a few more ways regulated small and mid-sized organizations are leveraging SASE to solve daily security and compliance challenges:
Rapid Mergers and Acquisitions
Law firms or healthcare groups that need to rapidly onboard acquired practices face the challenge of integrating diverse systems, users, and compliance profiles. With SASE, new mergers can be brought under a uniform security and compliance framework in hours, not months. SASE’s cloud-native controls allow standardized policies and easy extension of secure access, protecting sensitive data even as change happens.
Secure Third-Party Collaboration
Financial firms and CPAs frequently engage outside experts, consultants, and partners. SASE enables business leaders to grant time-limited, granular access to sensitive files and systems without opening the floodgates across the entire network. Every action taken by a third-party is logged, monitored, and easily revoked as needed.
Mobile and Field Workforce Security
Healthcare providers relying on remote nurses, home health visits, or mobile case workers can equip field staff with secure device profiles. With SASE, sensitive patient data is encrypted, device hygiene is enforced, and access to critical EHRs and care records can be permitted on the go, while still meeting HIPAA requirements.
Automated Response to Cyber Threats
A bank is alerted to a suspicious login from an unfamiliar country. With traditional tools, days might pass before action is taken. With SASE security’s real-time analytics and automated incident response, access from that device is blocked, the session is quarantined, and internal alerts are generated instantly, minimizing risk and stopping breaches before they spread.
Simplified Audit Preparation
Regulatory audits often inspire dread, especially when documentation is scattered across legacy email inboxes, spreadsheets, and local servers. With SASE, all access logs, policy changes, and incident reports are unified in a single dashboard. Audit preparation becomes a controlled, predictable process, not a fire drill.
The Future of SASE for SMBs in Regulated Industries
Trends in digital transformation show that secure access service edge will become even more vital as:
- Telemedicine expands and patient portals multiply, demanding advanced protections for distributed care
- Legal discovery increasingly happens remotely, requiring secure collaboration and seamless access rights management
- Finance adapts to digital payment systems and on-demand regulatory disclosures, with security platforms needing instant readiness for new compliance rules and rapid expansion
- Pharma and life sciences push for global research collaboration and cloud-first clinical trials, creating more data movement and complex access needs
With each innovation, regulators and cybercriminals adapt, so SASE solutions must evolve too. Expect further integration with artificial intelligence for adaptive threat hunting, privacy-preserving analytics, and predictive controls. Leading SASE providers will also invest in compliance automation, where updates for new laws can be swiftly propagated across organizations, minimizing manual effort and speeding up time to compliance.
Blueclone Networks continues to invest in this forward-looking model, evolving its managed IT and SASE service suite to help local SMBs lead in compliance and client trust. By choosing a partner deeply familiar with the realities of regulated businesses, organizations can focus on growth and service, knowing their edge and every connection to it is secure.
Should You Partner With Blueclone Networks?
If you’re asking yourself if Blueclone Networks is the right NJ-based IT solution for your business, consider these benefits
Maximum Uptime
Ensure your systems are always operational with minimal downtime.
Friendly and Prompt Communication
Approachable and responsive support for all your IT queries.
A US-Based SOC
Benefit from a Security Operations Center based in the United States.
Proven Reputation
Trust in our track record of delivering exceptional IT solutions.
Proactive Compliance
Stay compliant with the latest standards and practices.
Customized Plans for Each Client
Tailored IT strategies to meet your specific business needs.
Years of Relevant Experience
Leverage our extensive expertise for your IT success.

Serving Key Locations in New Jersey
We proudly serve various locations across New Jersey, including:
- Princeton, NJ: Offering specialized network support services to businesses in the Princeton area. Princeton is a hub for innovation, home to major institutions and tech startups.
- Lawrenceville, NJ: Providing comprehensive managed IT services tailored to the needs of Lawrenceville businesses.
- Hamilton, NJ: Delivering reliable managed IT services to support the growth and efficiency of Hamilton-based companies. Hamilton is one of the largest townships in NJ, known for its diverse business community.
Frequently Asked Questions About Secure Access Service Edge (SASE)
SASE, or secure access service edge, is a cloud-based system that brings together security and networking in one service. Unlike older tools that protect offices, SASE works everywhere, giving every user and device the same protections and access, whether in-office, remote, or using a mobile device. This is vital for regulated industries where policies and audits don’t stop at the office door.
Traditional firewalls and VPNs rely on a physical office perimeter and often miss modern risks, like remote workers or cloud accounts. SASE authenticates each user and device, no matter where they are, enforces policies in real time, and creates ready-made audit logs. It reduces breach risk and streamlines compliance tasks for SMBs, making governance less stressful.
Thanks to cloud delivery and managed options, SASE solutions are often more budget-friendly than maintaining and patching many separate security tools. SMBs can predict costs, enjoy fewer hardware headaches, and rely on expert partners for updates and monitoring, freeing staff to focus on day-to-day work.
Yes, SASE is specifically designed to enable secure access for employees, no matter where they work. Users get identical protections whether they’re at home, in a client’s office, or traveling, with no workarounds or risky exceptions required.
Focus on providers with deep experience supporting your industry’s compliance rules, local support for fast troubleshooting, comprehensive technology platforms (including Zero Trust and cloud integration), and clear, auditable logging. Ensure their solutions fit both your business model and regulatory profile.
About Blueclone Networks
Established in 2006, Blueclone Networks has been a trusted provider of IT solutions in New Jersey. Our commitment to excellence and customer satisfaction has positioned us as a leading network support company in NJ. We pride ourselves on delivering services that not only meet but exceed our clients’ expectations.





