Understanding SASE Architecture: The Foundation of Secure Access Service Edge
SASE architecture has become the go-to strategy for organizations seeking both robust protection and flexible connectivity. But what is the real meaning of SASE, and why is it gaining traction among healthcare clinics, legal offices, financial services, and pharmaceutical SMBs? Let’s unpack the core concepts behind Secure Access Service Edge and see how it defines the new era of network security.
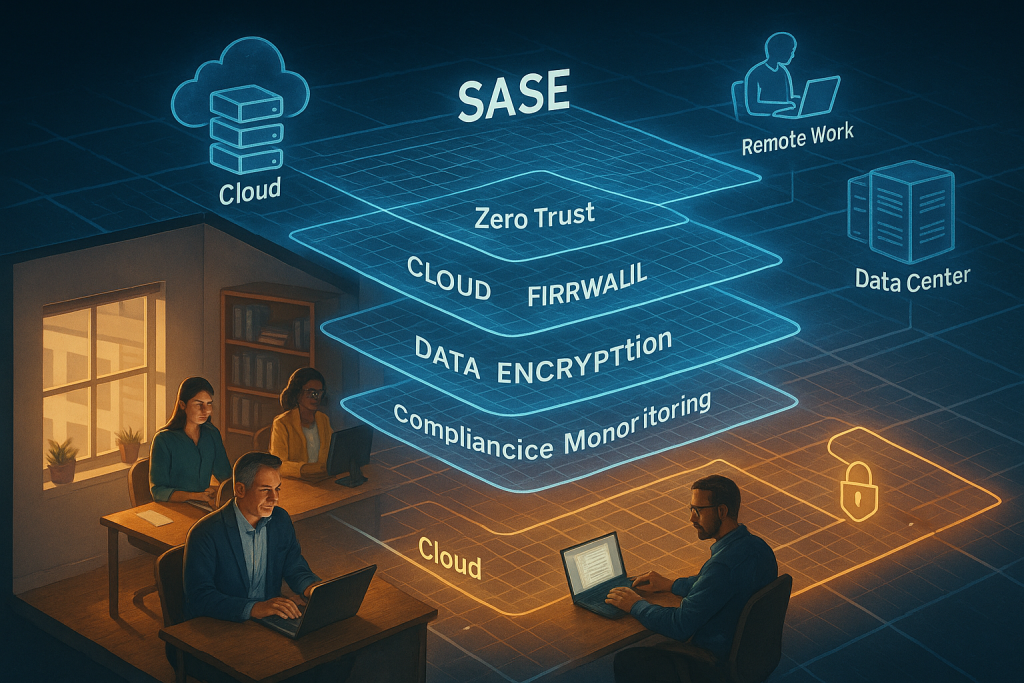
At its core, SASE architecture combines wide-area networking (WAN) capabilities with a full suite of security functions, all delivered from the cloud. The convergence is significant: instead of juggling independent network and security stacks, teams can streamline how employees and clients securely connect to resources, whether they’re working from a main office, a remote branch, or home.
SASE’s meaning goes beyond just cloud-based management. It embodies a shift to providing security and networking as an integrated, real-time service. This approach aligns well with the evolving demands of hybrid workforces and distributed digital assets in regulated sectors, where data compliance and secure connectivity must coexist without friction.
Key elements of SASE architecture include:
- Cloud-native security services: next-generation firewalls, secure web gateways, cloud access security brokers, and zero trust network access, all available without on-premises hardware headaches.
- Identity-driven policy enforcement: access is determined by robust checks on users, devices, locations, and the type of data being requested.
- Edge delivery: instead of routing traffic back to a central point, security is applied at the nearest possible location, reducing latency and improving user experience.
- Simple scalability: as organizations grow, add branches, or pivot quickly, the network and security boundaries move with them, no forklift upgrades required.
For SMBs in healthcare or legal fields, these architectural tenets solve a real problem: balancing the pressure for airtight compliance with the reality of tight IT budgets and limited in-house security expertise. According to Gartner’s 2025 update on SASE adoption, over 60% of enterprises and a rising share of SMBs are moving network-based security to this model to simplify operations and manage risk.
To get started tailoring SASE architecture to your compliance and security needs, Book an initial Discovery meeting with Blueclone Networks.
Core Components: What Makes Up SASE Network Security?
SASE network security is not a single product, but a framework composed of several interconnected services designed to work harmoniously from a cloud-native foundation. For those responsible for IT in SMB environments, especially in regulated industries, understanding each core piece clarifies what to prioritize and how to plan migration from legacy systems.
Network Components
Software-defined Wide Area Network (SD-WAN):
Traditional WANs struggle with modern data flow demands, especially as applications migrate to the cloud and users become more mobile. SD-WAN in SASE steers traffic dynamically, choosing the best path for performance while maintaining tight organizational control. Unlike old hardware routers, SD-WAN adopts a service-first approach, and users access their applications through the shortest, most secure route available.
Security Components
Cloud Access Security Broker (CASB):
Provides visibility and control over data and threats across all cloud services used by the organization, supporting regulatory demands like HIPAA or PCI-DSS.
Secure Web Gateway (SWG):
Inspects user internet traffic for unsafe content, malicious code, and access to risky sites, enforcing usage policies and blocking threats before they reach user devices.
Zero Trust Network Access (ZTNA):
Moves away from “all-or-nothing” network access, granting segmented entry to apps and resources only after verifying user identity, device health, and other criteria.
Firewall as a Service (FWaaS):
Modern firewalls delivered as cloud services, providing packet inspection, application awareness, and blocking of unwanted connections, regardless of user location.
When these capabilities are integrated, organizations create a security service edge that adapts in real time to changing risks and business needs.
Identity and Trust
SASE integrates authentication, single sign-on, and identity management as pillars. Trust is established dynamically based on real-time risk, there’s no longer a “trusted internal network” and “untrusted external world.” Every session begins with authentication and is continuously assessed, which matches perfectly with today’s hybrid work realities.
Direct Application Access
Unlike early VPN models that routed all traffic back to headquarters, SASE grants users direct access to cloud and SaaS applications, reducing delay and improving productivity. For in-house IT teams supporting remote clinics or attorneys working offsite, eliminating bottlenecks means staff stay efficient and clients’ needs are met without unnecessary wait times.
Midway through your SASE journey, when you’re evaluating vendors and want to map your current controls to modern cloud-native ones, it’s helpful to assess how each component supports your specific risk profile and compliance mandates. To gain a blueprint tailored for your organization, Book an initial Discovery meeting with Blueclone Networks now.
How SASE Enhances Cybersecurity Compliance in Regulated Industries
Cybersecurity compliance is more than ticking checkboxes. For sectors where sensitive financial, health, or legal records are managed, a single configuration slip can expose a business to fines, reputation harm, or regulatory audits. SASE architecture doesn’t just tighten network security – it actively helps regulated organizations meet stringent compliance goals without paralyzing daily operations.
Reducing Compliance Complexity
Traditional network setups scatter security controls across firewalls, proxies, VPN appliances, endpoint software, and more. SASE architecture converges protection, making it easier to prove compliance with laws like HIPAA, GLBA, SOX, or the SEC’s new incident disclosure rules. A centralized dashboard provides real-time visibility into every connection and policy enforcement activity, supporting both internal reviews and third-party audits.
Consistent Policy Enforcement
One compliance gap often seen in distributed environments is inconsistent policy application. For example, local clinics or law offices may run different versions of network protection, or branch offices may lack the same rule enforcement as headquarters. With SASE network security, organizations can push uniform access policies, data loss prevention (DLP) settings, and incident response protocols to every user, everywhere, instantly.
Evidence Collection and Visibility
Audits now frequently require proof, not just assurances, of proper security practice. SASE platforms continuously log who accessed what data, when, and from where, and flag risky behavior. Having granular logs and automated compliance reporting tools simplifies producing evidence for regulators and clients alike.
As highlighted by the National Institute of Standards and Technology (NIST) in its 2025 cloud security guidance, businesses using SASE models can more easily baseline their compliance status and detect anomalies quickly compared to legacy approaches.
Supporting AI and Cloud Modernization
Many SMBs in regulated industries are adopting cloud-based AI tools, analytics platforms, and external SaaS vendors. SASE’s architecture, by nature, supports secure on-ramps to these services while controlling data movement and enforcing audit readiness. For instance, a healthcare group rolling out an AI scheduling tool can apply real-time DLP rules at the edge, ensuring patient data never slips outside authorized channels.
Meeting compliance is an ongoing challenge in fields from finance to healthcare. With SASE at the network’s heart, SMBs gain a unified, proactive compliance story that stands up under scrutiny today and flexes to handle new regulations tomorrow.
Key Benefits of Adopting SASE Network Security for SMBs
The move to SASE network security is transformative for small and mid-sized organizations. While large enterprises have often led in new technology adoption, SASE offers concrete wins that fit the unique constraints and ambitions of SMBs, especially for those who must stretch IT resources and answer to strict regulations.
Simplified Management and Cost Efficiency
Legacy architectures required managing numerous point solutions, each with its own policy language, reporting, and upkeep. SASE brings central control, reducing overhead and the likelihood of human error. Automatic updates keep protections current, while cloud delivery models turn unpredictable capital expenses into predictable monthly costs, something CFOs and compliance officers alike can appreciate.
Agility for Hybrid and Remote Workforces
The days when every staff member worked within the four walls of a central office are long gone. SASE gives organizations the ability to securely onboard remote staff, bring new locations online, or support field teams without months of planning or hardware rollouts. This flexibility lets SMBs in legal and healthcare respond to changing client needs or regulatory shifts without delay.
Strengthened Threat Protection
SASE platforms excel at stopping phishing, ransomware, and data breaches closer to the user. Real-time threat intelligence, behavioral analytics, and malware filtering operate at the cloud edge, stopping threats before they reach endpoints or critical data stores. Unlike traditional tools that relied on simple IP blocklists or signature scans, modern security service edge capabilities use machine learning and cloud-based threat feeds to spot attackers who constantly change their tactics.
A recent report by Cybersecurity Magazine (2025) shows that organizations deploying full SASE networks saw a 45% reduction in successful phishing attacks and a 32% lower average breach cost, thanks to faster detection and response rates.
Improved User Experience
By routing data and enforcing policies at the closest possible cloud edge, SASE minimizes the delay users experience, boosting productivity. Direct SaaS and application access especially helps industries with time-sensitive tasks, such as healthcare patient chart lookups or real-time document sharing for legal casework.
Built-In Support for AI and Advanced Digital Tools
Many SMBs are under pressure to deploy AI-driven marketing, service, or scheduling systems. SASE provides the secure foundation these digital tools require, ensuring that sensitive information, whether it’s patient health data or confidential legal documents, remains under full organizational control.
Moving to SASE architecture positions SMBs not just to catch up with digital trends, but to lead with confidence, knowing the core of their IT is resilient and audit-ready.
SASE and the Future of SMB IT: Staying Ahead in an Evolving Threat Landscape
Business and cyber risks are evolving at a rapid pace. Phishing tactics, extortionware, insider risks, these pressures are increasingly targeting small and midmarket organizations, not just enterprise giants. SASE is a forward-looking architecture that equips organizations to meet current and future threats head-on with automation, speed, and adaptability built in.
As zero-day threats and regulatory requirements shift, SASE platforms can rapidly update controls via cloud orchestration, sidestepping the delays and gaps that plague traditional systems. Artificial intelligence modules, enabled by SASE’s scalable data processing, spot anomalies and automate responses in ways humans cannot match alone. Looking ahead, SASE’s architecture positions SMBs to more easily absorb new innovations, whether that’s IoT security, AI-powered identity, or quantum-resistant encryption, without another disruptive overhaul.
SASE and Data Privacy: Protecting Sensitive Information
With regulations such as HIPAA, GLBA, and GDPR enforcing strict standards around data privacy and breach notification, SASE’s data-centric focus provides a crucial risk-reduction advantage. Unlike fragmented legacy security, which may lack end-to-end encryption or granular controls, SASE offers in-line data loss prevention (DLP), continuous monitoring, and contextual access restrictions.
If a physician’s office accesses protected health data or a CPA transmits social security numbers, the SASE platform can automatically encrypt the data, apply DLP policies, and trigger alerts for unusual access locations or behaviors, mitigating insider threats or inadvertent leaks. In legal or financial management, SASE controls help demonstrate due diligence in handling PII, reducing both audit findings and real-world exposure.
A 2025 survey by Cybersecurity Magazine found that companies using SASE with integrated DLP experienced 40% fewer data privacy violations and slashed average detection/response times by more than half. As technology advances and attackers grow more sophisticated, this layered, policy-driven approach is quickly becoming the new baseline for those entrusted with sensitive information.
The Role of SASE in Business Continuity and Disaster Recovery
A modern SASE architecture isn’t just about better daily security, it offers distinct advantages when it comes to business continuity planning and rapid recovery from cyber or operational disruptions. For SMBs in healthcare, finance, or legal sectors, resilience is mission-critical. Downtime can mean lost revenue, regulatory penalties, or patient/client safety risks.
By consolidating policy enforcement in the cloud and leveraging distributed points of presence, SASE solutions make networks far less vulnerable to single points of failure. If a local outage or security breach impacts one branch, traffic and access can dynamically reroute through the cloud, maintaining connectivity and operations. Because vital data and controls reside offsite in secured, redundant environments, organizations are less susceptible to ransomware, hardware loss, or natural disaster incidents than those with aging on-premise setups.
SASE services can integrate tightly with backup/recovery platforms, allowing encrypted continuous backups, rapid fail-over, and tiered user re-access to critical systems. This holistic model fits perfectly with sector best practices recommended by NIST and industry regulators, who now expect not just preventive controls, but operational resilience and testable incident response plans.
How to Implement SASE Architecture: Steps for SMBs and In-House IT Teams
Understanding SASE meaning is one thing; implementing it wisely is another. For IT leaders at small and mid-sized firms, especially those juggling compliance alongside daily network management, the right roadmap matters. Here’s how to approach a successful SASE deployment, with practical guidance for working within resource, time, or legacy system constraints.
Step 1: Map Your Current Network and Security Landscape
Begin with a thorough inventory of existing WAN connections, endpoint types, cloud applications in use, and all legacy security solutions. Catalog compliance requirements: for example, HIPAA for medical practices, PCI-DSS for financial offices, or FINRA rules for legal firms handling sensitive client data.
Step 2: Identify Priority Risks and Compliance Gaps
A gap analysis helps pinpoint where current systems fall short. It might reveal inconsistent VPN policies, remote users lacking standardized endpoint security, or shadow IT (unsanctioned applications or data sharing). For regulated SMBs, map findings directly to compliance mandates, many regulations now require explicit logging, continuous risk monitoring, and response protocols that traditional architectures cannot efficiently support.
Step 3: Establish Clear SASE Goals
Set objectives: Is your primary motivator stronger breach protection? Simplification of audit processes? Seamless support for remote teams? Prioritize business outcomes to avoid feature overload; not every SASE function must roll out simultaneously.
Step 4: Engage Internal and External Stakeholders Early
Bring in legal, compliance, and C-suite leaders alongside IT staff. For regulated firms, collaboration with external auditors or compliance consultants upfront smooths both migration and future audit cycles. Consider co-managed IT providers who offer deep SASE expertise and can share the heavier lifts, from selecting the right vendor to guiding technical implementation.
Step 5: Choose the Right SASE Vendor and Services
Evaluate vendors based on their ability to meet your industry’s compliance specifics (e.g., integrated audit logging, policy granular enough for partitioned data, high service uptime). Look for support models that include 24/7 helpdesk, local expertise, and transparent billing. In some sectors, in-region data residency and advanced encryption options are must-haves.
Step 6: Pilot Test and Transition in Phases
Test SASE on a subset of users or one branch location, measuring user experience, policy adherence, and compliance reporting accuracy. Review incidents closely; refine policies as needed. Once confidence is high, expand to other endpoints, branch offices, and applications at a pace your IT team or MSP can manage.
Step 7: Train and Support End-Users
Changing security models, even for the better, can cause confusion. Run short workshops or onboarding sessions for staff, focusing on authentication changes, direct SaaS access improvements, or new user portals. Keep communication lines open for questions as you scale up.
Real-world example: A Princeton-area legal practice with satellite offices piloted SASE with a focus on secure client communication and success-based access to case files. By consulting both compliance staff and frontline paralegals during the rollout, they cut response times on legal matters while ensuring every client interaction was logged per new regulatory expectations.
To build an implementation timeline that matches your organization’s risk, scale, and compliance needs, Book an initial Discovery meeting now.
Common SASE Questions Answered: FAQ for SMB Decision Makers
SASE stands for Secure Access Service Edge. It’s a cloud-native framework that brings together networking and security services like SD-WAN, firewalls, secure web gateways, and identity controls, providing scalable, real-time protection and policy enforcement wherever users and data reside.
SASE simplifies compliance efforts by centralizing policy management, automating evidence collection, and enforcing consistent controls across locations and users. This makes meeting regulatory requirements (for example, HIPAA, PCI, FINRA) more manageable for smaller IT teams.
Yes. One of SASE’s strengths is its flexibility. Security policies are enforced equally whether users are on-premises, at home, or accessing cloud applications while traveling, making it ideal for organizations with distributed staff or evolving workplace models.
Unlike older network security models, SASE treats every access request as potentially risky and applies security closer to the user or device. This accelerates secure cloud adoption, boosts user productivity, and limits the attack surface area.
Begin by assessing your current network, applications, and compliance mandates. Identify existing gaps and define clear goals for SASE adoption, such as improving compliance reporting or simplifying management. Engaging a trusted IT partner experienced with SASE and regulated industries will smooth the transition.